O-Cloud – Open Cloud Requirements for Open RAN Operators
Introduction
As per definition Open Cloud or O-Cloud is a cloud computing platform consist of physical infrastructure nodes that meet O-RAN requirements to host O-RAN CUs, DUs functions, supporting software and the appropriate management and orchestration functions. An O-Cloud Node is a collection of CPUs, memory, storage, NICs, BIOS, BMCs, and accelerators to offload computational intense functions like FEC.
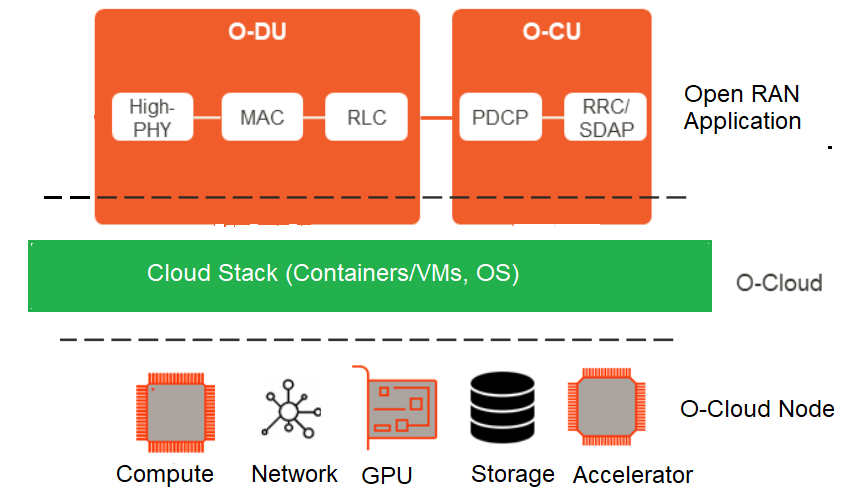
O-Cloud as a terminology refers to a collection of O-Cloud resource pools at one or more location. It includes functionality to support both deployment plane and management. O-Cloud unlock vendor locking and allow any vendor can host its application on it.
Open Cloud Requirements for Open RAN Operators
-
Deployment Modes Support
- Bare Metal Implementation: Open Cloud shall support Open RAN implementation on Bare Metal
- Multi-model: Open Cloud shall provide the possibility to select a deployment model among these:
- Control and Data planes are collocated on a unique edge site
- Control planes are on a centralized site and data planes are on a unique edge site
- Control planes are on a centralized site and data planes are on several edge sites
- Multi-tenancy and Isolation: Open Cloud shall provide and enforce appropriate isolation for critical components at compute/network/storage physical infrastructure level e.g. as imposed by Regulators for emergency services and/or public-safety departments, hospitals
- Scalability: Open Cloud should provide auto scaling solutions at node level for central and edge/distributed deployment
- Multi-cluster workload lifecycle: Open Cloud shall support the management of the deployment and lifecycle of workloads on multiple clusters
- Inter clusters connectivity and Load Balancing: Open Cloud shall manage the network interconnection of CNF services hosted on distributed clusters. Manage the Load Balancer between distributed CNF features including support for auto scaling and site resiliency
- Management Operation Support
- Board Management: Open Cloud shall contain an Infrastructure Management Service, which interfaces to server and switching HW utilizing vendor independent interfaces
- Configure Management : Open Cloud shall support configuration management to manage HW CPU core, storage and memory including Auto-discovery of new servers, installation parameters such as console, root disks, core configuration, memory, huge-page assignments on each server node, Network interfaces and storage assignments, Hardware discovery of CPUs, cores, storage, network ports, hardware accelerators, etc, Virtual-to-physical CPU core and NUMA node pinning, Virtual NUMA topology configuration, Huge-page memory, interrupt and thread pinning to virtual and physical cores
- Host Management: Open Cloud shall support Host management to manage host failure detection and recovery, cluster connectivity failure detection and recovery, HW sensors and faults
- Service Management: Open Cloud shall support monitoring of critical platform infrastructure services and processes, and automatic recovery of failed platform infrastructure services and processes
- HW Management: Open Cloud shall support High-availability services for supporting cloud platform redundancy
- Fault Management: Open Cloud shall support Cloud platform infrastructure alarm and fault management and ability to set, clear, query, filter, suppress, log and collect alarms
- Software Management: Open Cloud shall support the ability to deploy software updates; Support for rolling updates across all nodes of the local Open Cloud. For assuring SW upgrade procedures, we may need to migrate firstly VMs running in the local O-Cloud and drain the nodes for containers.
- User Management: Open Cloud shall support user authentication and authorization, and Isolation of control and resources among different users
- Feature Management: Open Cloud shall support detection and setting node-level policies to align resource allocation
- HW Acceleration Management: Open Cloud shall support for managing hardware accelerators, and updating accelerator firmware
- CaaS Cluster Management: Open Cloud shall support Kubernetes cluster life cycle management and bare metal integration
- Container Management (K8S): Open Cloud shall be able to define K8S clusters based on different worker node class of service (standard, network intensive, FPGA,GPU)
-
Time Synchronization Support
- Support GNSS for distributing phase, time and synchronization for distributed scenario
- Support Precision Time Protocol (PTP) for distributing phase, time and synchronization and compliance with G.8275.1
- Support Synch E for distributing phase synchronization and compliance with compliance with G.8275.1
-
Kubernets plugin Support
- SR-IOV: O-Cloud shall support SR-IOV and provides a low-latency interface for both packet I/O and acceleration interfaces
- PCI Pass-through: O-Cloud shall support PCI pass-through in case only one container needs to use the networking interface to provide high performance and low latency without using a virtual switch.
- Multus: O-Cloud shall support the Multi Networking feature in Kubernetes using CRD-based network objects in Kubernetes
- CPU Manager: O-Cloud shall support basic core affinity for CNFs. It is required to pin real- time threads to specific CPU cores in order to improve performance and meet real-time latency
- FPGA: O-Cloud shall support FPGA Device plugin for FPGA passthrough, only if specific hardware support is required
- HugePage: O-cloud platform shall support ability to allocate the necessary amount of the faster memory (a.k.a. HugePages) to the container, and also to relinquish this memory allocation in the event of unexpected termination
- DPDK: O-Cloud shall support the implementation of userspace networking for K8S containers, e.g. DPDK
-
Security
- Zero Trust: Open Cloud shall follow the Zero Trust Architecture (ZTA) approach and shall be based on a robust, secure and trusted cloud native hardware and software infrastructure that delivers true defence in depth for functions and data through the entire information processing lifecycle, including:
- Securely Hardened O-Cloud platform e.g. hardened Host Operation System/Kernel
- Integrate automated security testing into CI/CD process
- Secure deployment of network functions (workloads), e.g. apply security update regularly, once security vulnerability found in the containers, and update the container image accordingly
- Secure storage of data
- Secure communications between services and functions
- Secure configuration of the cloud infrastructure assets
- Zero Trust: Open Cloud shall follow the Zero Trust Architecture (ZTA) approach and shall be based on a robust, secure and trusted cloud native hardware and software infrastructure that delivers true defence in depth for functions and data through the entire information processing lifecycle, including:
-
Others
- Cost & Energy/Green Management: O-Cloud shall optimize and reduce energy consumption, minimizing costs
- Infrastructure Service Inventory: Open Cloud shall support Infrastructure Service Inventory, which describes the whole infrastructure, its components, its distribution. It shall describe available clusters as well as clusters used by an app. This inventory is synchronized with any change at the infrastructure and at the clusters levels in terms of creation, availability, location, resources, app usage, .
Related Posts:
- IEEE 1588: Precision Time Protocol (PTP) for Telecom Networks
- Timing Application – ptp4l, phc2sys and pmc
- O-RAN RU Reference Architecture
- O-RU Category A and Category
- O-RU Digital Front Solution (DFE) Solution from Xilinx
- O-RAN Distributed Unit (O-DU) Reference Architecture
- Cloud RAN Orchestration and Management