Security in Kubernetes – Service Account
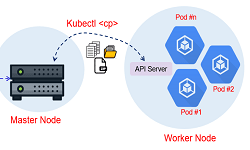
A mutli-node kubernetes cluster is deployed with different K8s services like kube- schedular, API-server,controller-manager, etcd, etc. on top of Master Node and with the help of kubectl command user can access the cluster but before access user have to perform
authentication and based on RBAC & IAM user get the power & privileged. kubectl program first point of contact inside k8s is API server.
In the Kubernetes cluster, any processes or applications which resides within the pod want to can access the k8s cluster but do not have Username/Password can be authenticated by the API server, using a Service Account.
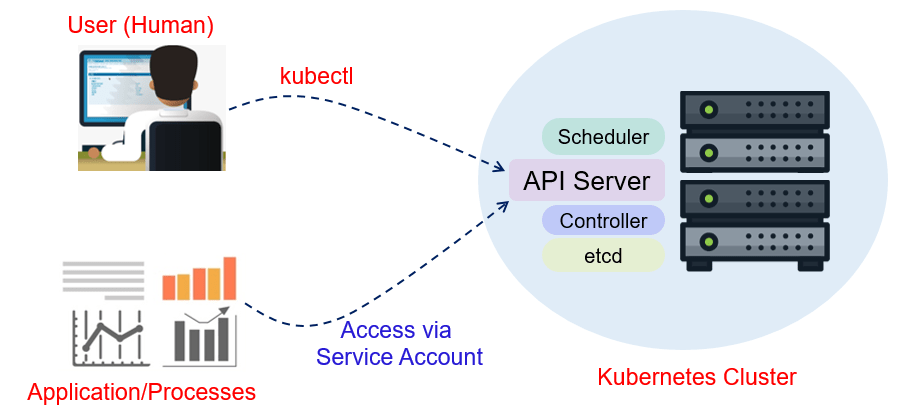
For a practical use case we can consider Monitoring tool like Prometheus inside the cluster as a Pod and this pod communicate with K8s to collect different matrices like CPU, RAM usage by different applications and on top of these matrices Kibana and Grafana create interactive graphs. So here, Prometheus will contact with K8s with the help of Service Account & Token.
Types of Services Accounts
There are two types of service accounts in Kubernetes
- User Account: It is used to allow humans, to access the given Kubernetes cluster. Any user needs to get authenticated by the API server to do so. A user account can be an admin or a developer who is trying to access the cluster level resources.
- Service Account: It is used to authenticate machine level processes to get access to our Kubernetes cluster. The API server is responsible for such authentication to the processes running in the pod
Service Accout with Example
Let understand the Service account resource with practical example:-
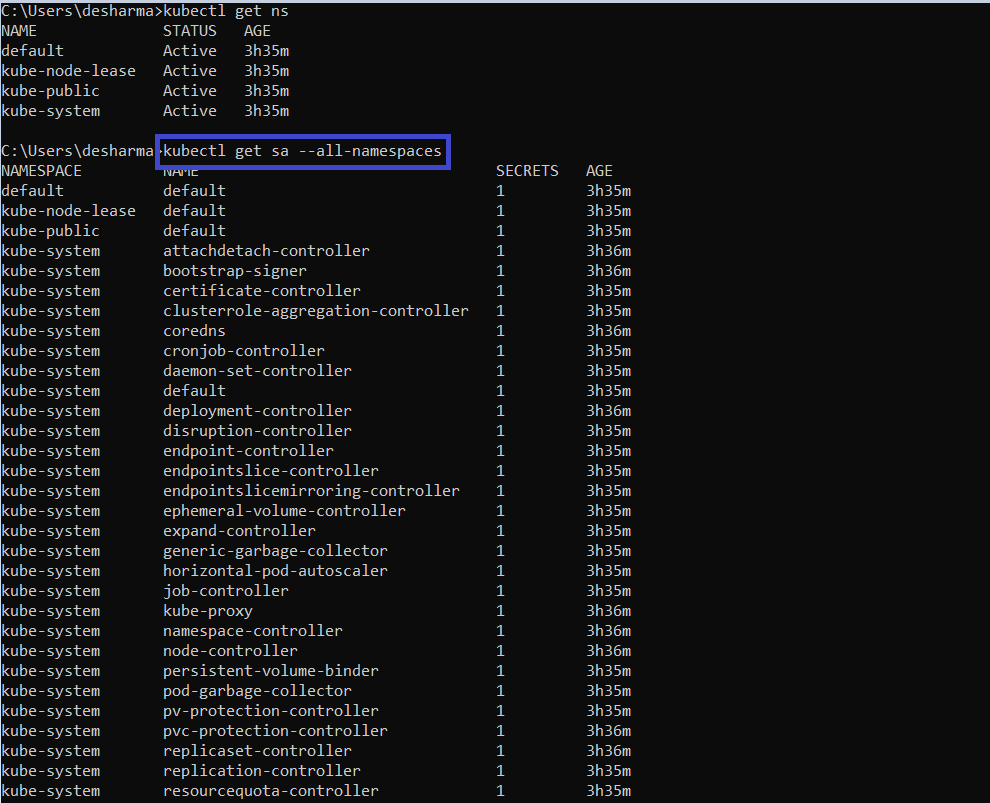
- Below mentioned command is used to check various application or processes which used the service account to communicate with k8s master node.
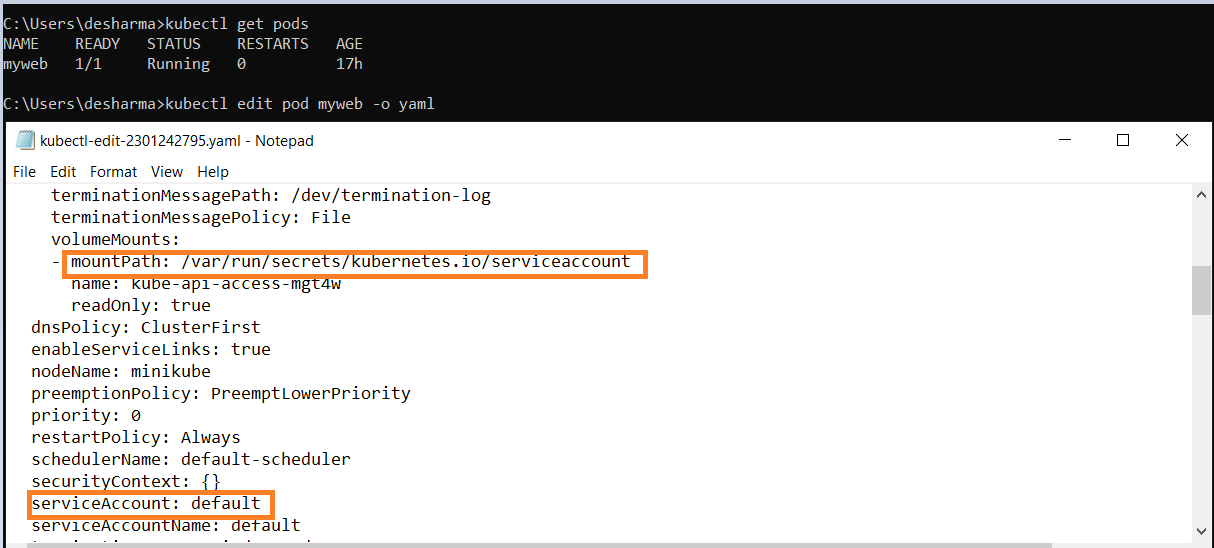
- Lets check the YAML file for the default Service account default-token-4m11j is written inside secret

- Secret objet type provides a mechanism to hold sensitive information such as passwords. Secrets decouple sensitive content from the pods. We can mount secrets into containers using a volume plug-in.
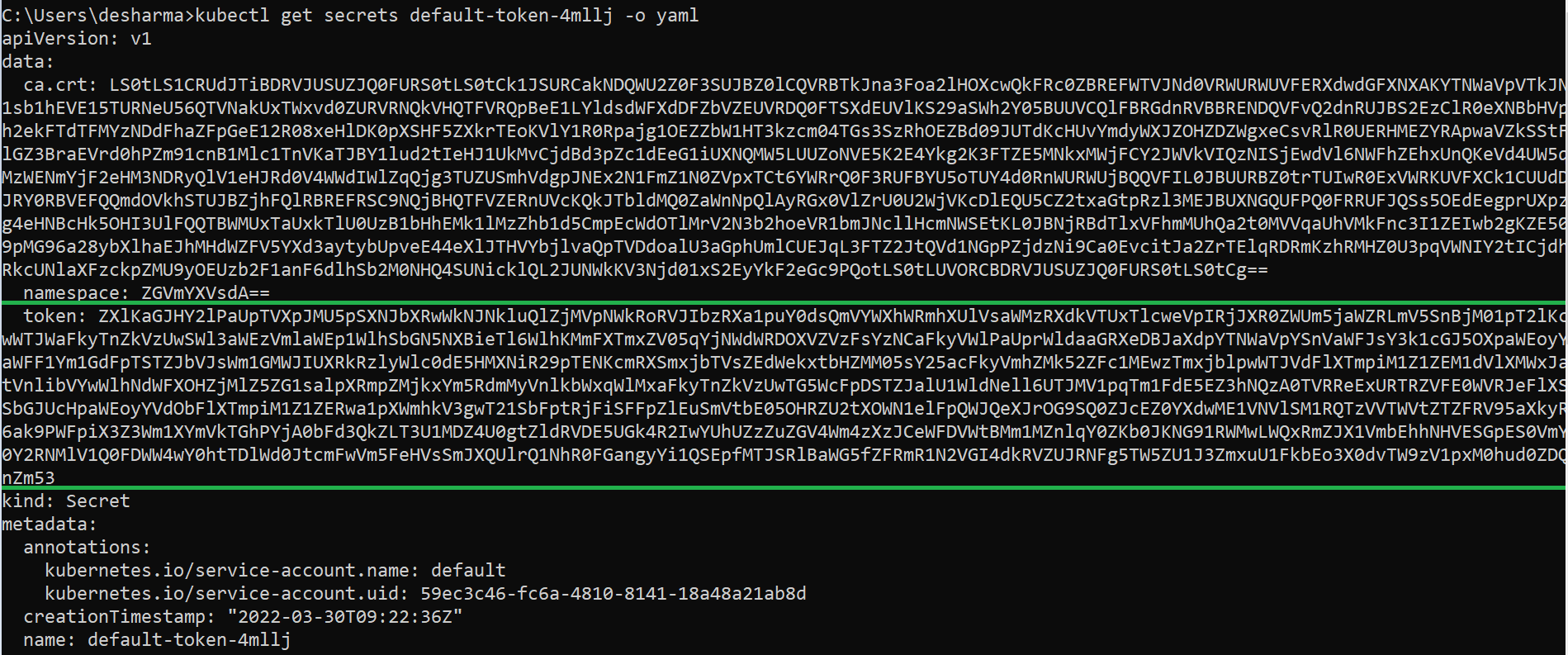
- myweb is the pod name inside YAMl file key-value pair (Service account name: default) is mention and mount path for same as /var/run/secerets/kubernetes.io/serviceaccount serviceaccount/
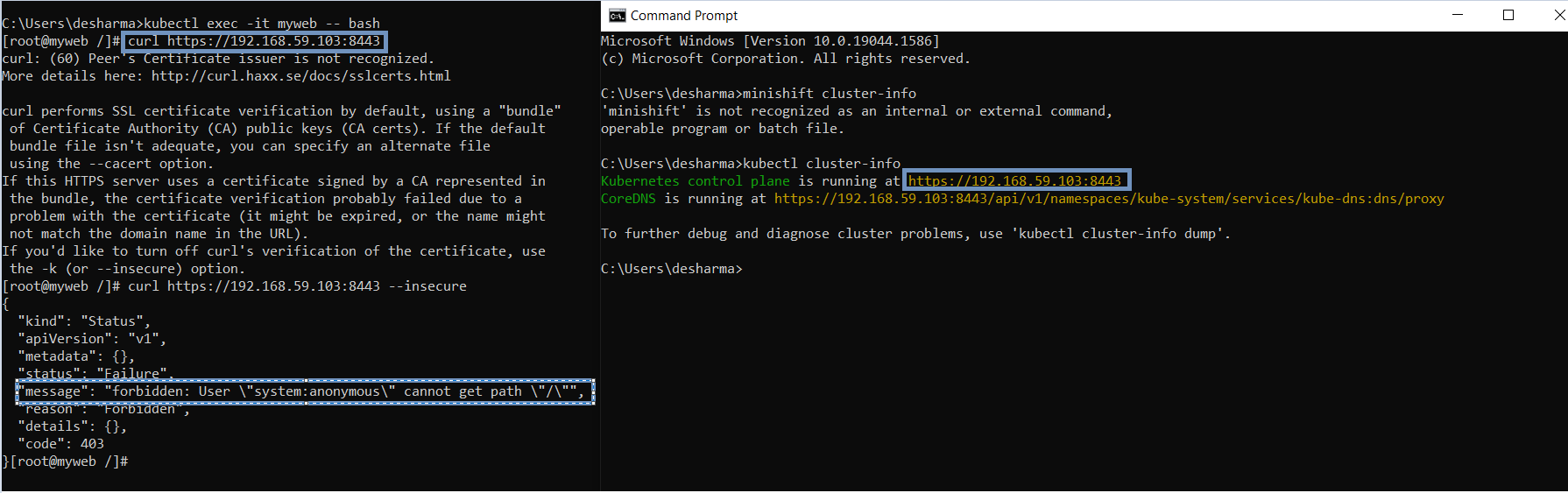
- Single node cluster is running at https://192.168.59:103:8443 curl is a process try to access the cluster but without token user will get response as anonymous/forbidden.
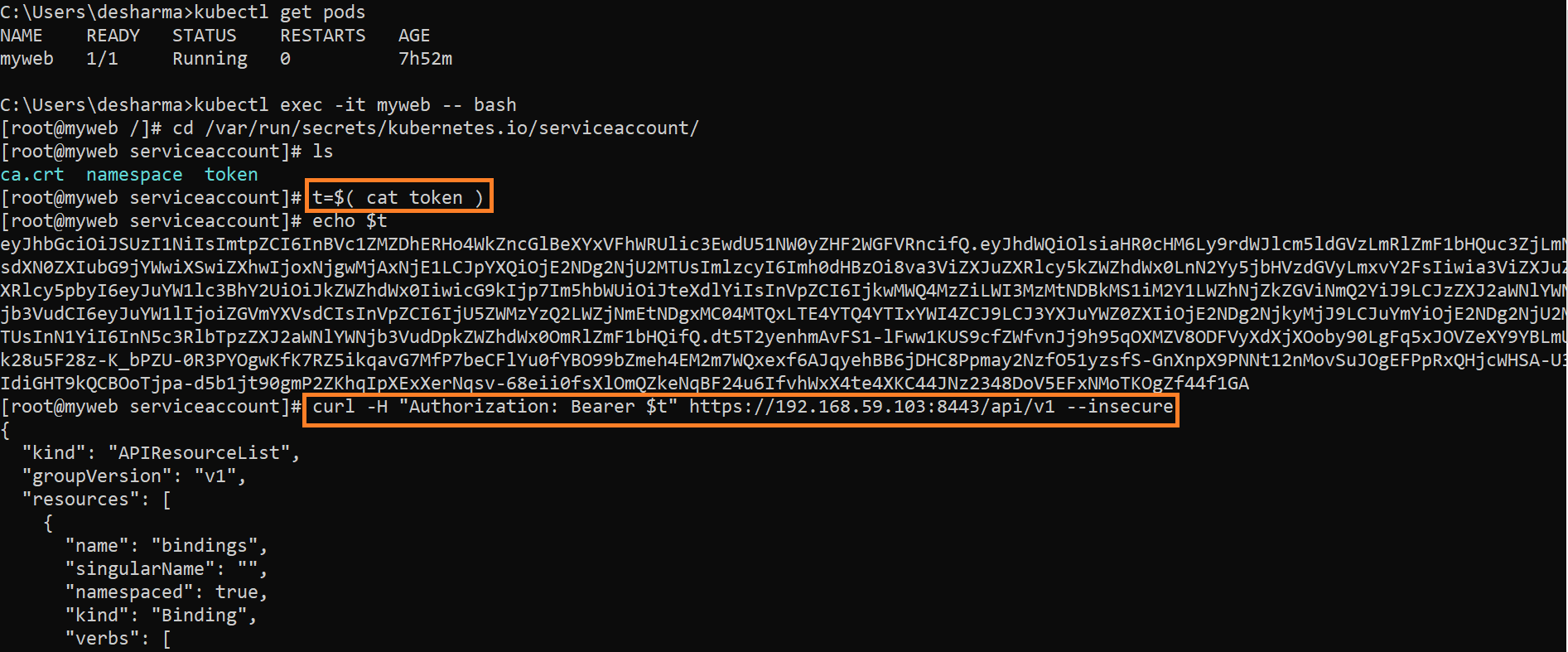
- When tried to retrive the token from mount path /var/run/secrets/kubernetes.io/serviceaccount/ and retrive that Inside a variable “t” so now we have token inside “t”
- Now curl process tried to accesss the cluster with token and able to communicate or access the K8s cluster via API server
Key Learnings
- In today world Security is the main area of concern for most of the real world scenerio process & application have to communicate with K8s master node via API server
- Program & Processes don’t have capabilites to use user name and Password for Authentication
- So they used Service account & Token to communicate with the K8s cluster
Article is submitted by Deepak Sharma