5G Identifiers SUPI and SUCI
5G SUPI and SUCI
In telecommunication systems, network operator allocate to each SIM card a unique identifier, known up to the 4G as an IMSI (International Mobile Subscriber Identity) and for the 5G as a SUPI (Subscription Permanent Identifier). As authentication between a user and its network provider is based on a shared symmetric key, it can only take place after user identification. However, if the IMSI/SUPI values are sent in plaintext over the radio access link, then users can be identified, located and tracked using these permanent identifiers.
To avoid this privacy breach, the SIM card is assigned temporary identifiers (called Temporary Mobile Subscriber Identity (TMSI) until 3G systems and GUTI for 4G and 5G systems) by the visited network. These frequently-changing temporary identifiers are then used for identification purposes over the radio access link. However, there are certain situations where authentication through the use of temporary identifiers is not possible e.g. when a user registers with a network for the first time and is not yet assigned a temporary identifier, another case is when the visited network is unable to resolve the IMSI/SUPI. from the presented TMSI/GUTI.
An active man-in-the-middle adversary can intentionally simulate this scenario to force an unsuspecting user to reveal its long-term identity. These attacks are known as “IMSI catching” attacks and persist in today’s mobile networks including the 4G LTE/LTE-Adv.
Solution to IMSI Catchers in 5G
IMSI – catching attacks have threatened all generations (2G/3G/4G) of mobile telecommunication for decades. As a result of facilitating backwards compatibility for legacy reasons, this privacy problem appears to have persisted. However, the 3GPP has now decided to address this issue, albeit at the cost of backward compatibility. In case of identification failure via a 5G-GUTI, unlike earlier generations, 5G security specifications do not allow plain-text transmissions of the SUPI over the radio interface. Instead, an Elliptic Curve Integrated Encryption Scheme (ECIES) – based privacy-preserving identifier containing the concealed SUPI is transmitted. This concealed SUPI is known as SUCI (Subscription Concealed Identifier )
Subscription Permanent Identifier (SUPI)
A SUPI is a 5G globally unique Subscription Permanent Identifier (SUPI) allocated to each subscriber and defined in 3GPP specification TS 23.501. The SUPI value is provisioned in USIM and UDM/UDR function in 5G Core.
A Valid SUPI can be either of following
- An IMSI (International Mobile Subscriber Identifier) as defined in TS 23.503 for 3GPP RAT
- NAI (Network Access Identifier) as defined in RFC 4282 based user identification as defined in TS 23.003 for non-3GPP RAT
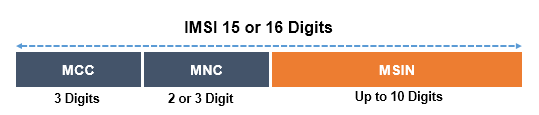
A SUPI is usually a string of 15 decimal digits. The first three digits represent the Mobile Country Code (MCC) while the next two or three form the Mobile Network Code (MNC) identifying the network operator. The remaining (nine or ten) digits are known as Mobile Subscriber Identification Number (MSIN) and represent the individual user of that particular operator. SUPI is equivalent to IMSI which uniquely identifies the ME, is also a string of 15 digits.
Subscription Concealed Identifier (SUCI)
Subscription Concealed Identifier (SUCI) is a privacy preserving identifier containing the concealed SUPI. The UE generates a SUCI using a ECIES-based protection scheme with the public key of the Home Network that was securely provisioned to the USIM during the USIM registration.
Only the MSIN part of the SUPI gets concealed by the protection scheme while the home network identifier i.e. MCC/MNC gets transmitted in plain-text. The data fields constituting the SUCI are following

- SUPI Type: consisting in a value in the range 0 to 7. It identifies the type of the SUPI concealed in the SUCI. The following values are defined
- 0: IMSI
- 1: Network Access Identifier (NAI)
- 2 to 7: spare values for future use.
- Home Network Identifier: identifying the home network of the subscriber. When the SUPI Type is an IMSI, the Home Network Identifier is composed of MCC and MNC. When the SUPI type is a Network Access Identifier, the Home Network Identifier consists of a string of characters with a variable length representing a domain name. e.g. user@techno.com
- Routing Indicator: It is consist of 1 to 4 decimal digits assigned by the home network operator and provisioned within the USIM.
- Protection Scheme Identifier: It is consist of a value in the range of 0 to 15 and represented with 4 bits
- null-scheme 0x0
- Profile <A> 0x1
- Profile <B> 0x2
- Home Network Public Key Identifier: It is consist of a value in the range 0 to 255. It represents a public key provisioned by the HPLMN and it is used to identify the key used for SUPI protection. In case of null-scheme being used, this data field shall be set to the value as 0
- Protection Scheme Output : It is consist of a string of characters with a variable length or hexadecimal digits, dependent on the used protection scheme
5G Identity Exchange between UE and Network
The subscriber identification mechanism allows the identification of a UE on the over the air radio interface by means of the SUCI. The Identify exchange between UE and Network is shown in following figure.
When UEs tries to register first time, UE encrypt SUPI into SUCI and send a Initial Registration Requested with SUCI. AMF forward this SUCI to AUSF & UDM to retrieve the SUPI with Authentication Request. AUSF shall reply with Authentication Response with SUPI information. Further AMF generates a GUTI for this SUPI and keeps the GUTI to SUPI mapping for further registrations or PDU session requests.

In subsequent Registration request UE send registration request with GUTI. Now there can be two possible scenarios.
- AMF able to generate SUPI using GUTI and SUPI mapping
- AMF not able to generate SUPI
In first case, AMF generate SUPI using GUTI and authentication with AUSF can be completed using SUPI. In second case when the UE is not identifiable using GUTI at AMF, AMF request UE for identity request and UE then may respond with the Identity Response, containing the SUCI.
References
- 3GPP TS 23.501 5G;. System Architecture for the 5G System
- The Evolution of security in 5G – 5G America Whitepaper
- Identity Confidentiality in 5GMobile Telephony Systems -Whitepaper
Related Posts
- 5G System Connection Management: CM-Idle and CM-Connected
- 5G NR Global Unique Temporary Identifier (GUTI)



