tcpdump for Linux System – A Tool for IP Packet Analysis
tcpdump
In my experience as a protocols test engineer, I have often found issues related to network connectivity, throughput loss, protocol procedure failures, having a challenge to troubleshoot and needs to verify IE level details. For these situations, tcpdump is a great tool. This is a command line utility that allows to capture the live TCP/IP packets going through an network interface and can also be saved to a pcap file for offline analysis using Wireshark tool. It is a very well known tool for IP packet capture in Linux systems.
In this article, we’ll look at some of tcpdump’s most common features.
tcpdump Utility Key Pointers
- It is a command line tool, very handy to troubleshooting on network and protocol level troubleshooting
- Command line tool makes it ideal to run in remote servers or devices for which we do not have GUI access
- This includes many options (runtime, save file) and filters (port, protocol, interface choice) so user can use as per requirement
- It allows to capture the live TCP/IP packets going through an network interface and can also be saved to a pcap file for offline analysis using Wireshark tool
Most OS have tcpdump command pre-installed, if it is not installed you can install using following commands.
- sudo yum install tcpdump (RedHat based Linux OS)
- sudo apt-get install tcpdump (Ubuntu/Debian OS)
tcpdump command arguments
The command run with some arguments and selection of these argument depend on what information you want to capture using tcpdump e.g. shown in hand-on examples. Following list provide details and meaning of some of most commonly used arguments.
- -i = Interface
- -w = Write to a file
- -r = Read a file
- -c = count for packet capture
- src= source
- dst= destination
- port = application port number for packet capture
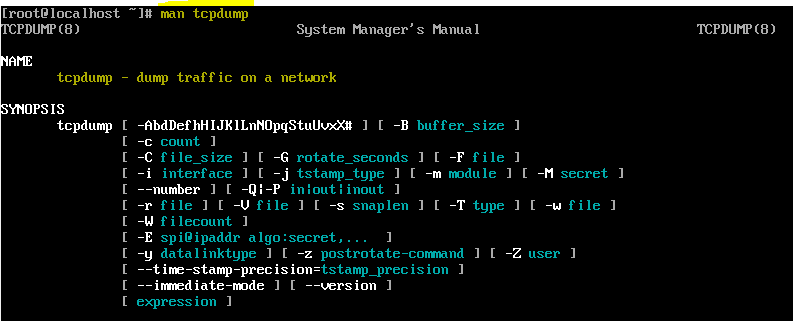
MAN for tcpdump
In linux system if you are not aware about the details of any application. you an do man to provide user manual for it. Following is the MAN for tcpdump.
Common Command Examples
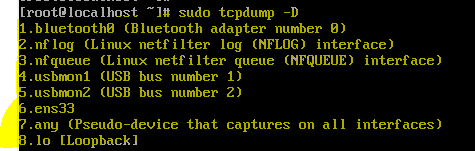
- Checking the available interfaces :
- sudo tcpdump -D
- Capturing packets on a specific network interface
- sudo tcpdump -i <interface name> in below image selected interface is ens33
- sudo tcpdump -i ens33

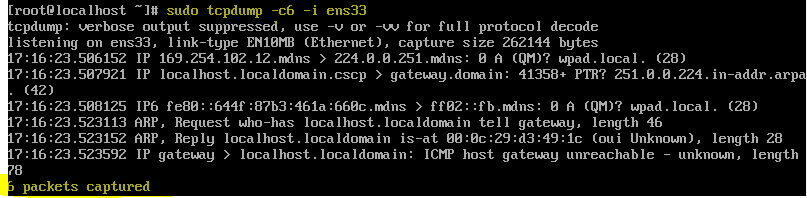
- Capturing limited numbers packets on a specific network interface
- sudo tcpdump -c <no. of packets> -i <interface name>
- sudo tcpdump -c 6 -i ens33
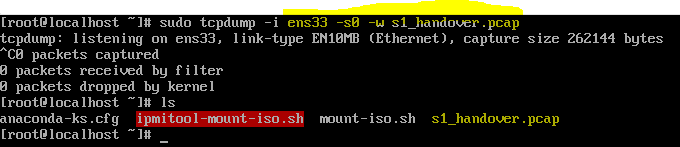
- Capturing packets on a specific network interface and saving to a Wireshark file
- sudo tcpdump -i <interface name> -s0 -w < filename.pacp >
- sudo tcpdump -i ens33 -s0 -w s1_handover.pcap
- Applying Filter with specific protocol
- sudo tcpdump -i <interface name> -s0 -w < filename.pacp > <protocol>
- sudo tcpdump -i ens33 -s0 -w s1_setup.pcap sctp
- Applying multi filter with source IP, specific port and destination IP
- sudo tcpdump -i src <ip address> port < port number> dst <ip address> -s0 -w < filename.pacp >
- sudo tcpdump -i src 192.168.3.1 port 36422 dst 192.168.3.100 -s0 -w s1_setup.pacp
- Displaying run time packets link level header in HEX and ASCII format
- sudo tcpdump -xx -i <interface name>
- sudo tcpdump -xx -i ens33
Related Posts



