5G Authentication and Key Management
Secure communication in any cellular network can be achieved with help of AKA procedure. AKA is Authentication and Key Management procedure which involve mutual authentication between User Device and the network and derive crypto keys to protect the U-plane and C-plane data. Each telecom “G” defines some authentication method to allow only legitimate users to access network and reject un-authorized users. 3GPP defined EPS-AKA for 4G LTE and similarly for 5G following three authentication methods are defined
- 5G-AKA: 5G-Authentication and Key Management
- EAP-AKA: Extensible Authentication Protocol – Authentication and Key Management
- EAP-TLS: Extensible Authentication Protocol – Transport Layer Security
Why we need new AKA procedures in 5G?
Security and privacy concerns are very critical and importance for any new technology to succeed. 5G networks availability is becoming reality throughout the world and new use cases are getting introduced. Security and privacy issues with previous “G” RANs network, have been extensively studied by Security Experts and Researchers. A few of such issues are listed below.
- Network spoofing : A faked base station can broadcast a different tracking area code with a stronger signal strength to lure user equipment (UE) away from its legitimate cellular network to register with the faked base station
- Lack of confidentiality: By intercepting certain OTA signaling messages users privacy can be compromise. E.g. paging information, which is not encrypted, can be used to detect the presence of a particular user and even to track the user to a precise location
To mitigate such issues, standardization bodies like 3GPP has defined an AKA protocol and procedures that support user authentication, signaling integrity, and signaling confidentiality, among other security properties. The 3GPP AKA protocol works on challenge-and-response authentication protocol based on a symmetric key shared between a User and a Network. After the mutual authentication between a User and a home network, crypto keys are derived to protect further communication between a User and a serving network, including C-plane and U-plane data.
5G AKA Framework
3GPP has proposed a Service Based Architecture for Core network with new network entities and new services to support a unified authentication framework. This framework makes 5G AKA procedure suitable for both open and access-network agnostic using three authentication methods namely 5G-AKA, EAP-AKA’, and EAP-TLS. The Frameworks allows multiple security contexts which can be established with one authentication execution, allowing the UE to move from a 3GPP access network to a non-3GPP network without having to be reauthenticated. The framework includes following network function within Core network relevant to 5G authentication.
- Access and Mobility Management Function (AMF): It receives all connection and session related information from the User Equipment (UE) (N1/N2) but is responsible only for handling connection and mobility management tasks.
- Security Anchor Function (SEAF): It resides within serving network (closely with AMF) and acts as “middleman” during the authentication process between a UE and its home network. It can reject an authentication from the UE, but it relies on the UE’s home network to accept the authentication.
- Authentication Server Function (AUSF): It is within a home network and performs authentication with a UE. It makes the decision on UE authentication, but it relies on backend for computing the authentication data and Keys when 5G-AKA or EAP-AKA’ is used.
- Unified data management (UDM): It is similar to HSS/HLR entity and hosts functions related to data management, such as the Authentication Credential Repository and Processing Function (ARPF), which selects an authentication method based on subscriber identity and configured policy and computes the authentication data and Keys for the AUSF whenever required.
- Subscription Identifier De-concealing Function (SIDF): This function decrypts a SUCI to obtain its long-term identity known as the SUPI, e.g., the IMSI. In 5G, a subscriber long-term identity is always transmitted over the radio interfaces in an encrypted form. More specifically, a public key-based encryption is used to protect the SUPI. Therefore, only the SIDF has access to the private key associated with a public key distributed to UEs for encrypting their SUPIs.
- Non-3GPP Interworking Function (N3IWF): N3IWF is an newly introduced entity which acts as a VPN server to allow the UE to access the 5G core over untrusted, non-3GPP networks through IPsec tunnels. There can be multiple security contexts can be established with one authentication execution, allowing the UE to move from a 3GPP access network to a non-3GPP network without having to be reauthenticated.
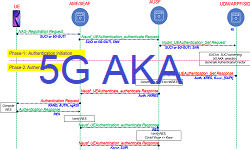
5G-AKA Authentication Procedure
3GPP has defined new authentication-related services for 5G. For example, the AUSF provides authentication service through Nausf_UEAuthentication, and UDM provides its authentication service through Nudm_UEAuthentication services. Following figures show the sequence and authentication vector including a subset of data.
5G AKA and EAP-AKA’ are mandatory 5G primary authentication methods. Other EAP based authentication methods can be used optionally as well. To keep it simple for understanding lets us divide the authentication procedure in two phases.
two phases, see Figure 5.
-
- Phase 1: 5G authentication initiation and selection of authentication method
- Phase 2: Mutual authentication between the UE and the network
- During phase 1, The SEAF may start the authentication procedure after receiving NAS signaling message (Registration Request, Service Request etc.) from the UE.
- The UE should send the SEAF a temporary identifier as a GUTI or an encrypted permanent identifier such as SUCI if GUTI has not been allocated by the s network. In 5G, UE’s permanent identifier e.g. the IMSI, is not allowed to sent in clear text over the radio networks. This consideration is a major security improvement over prior generations such as 4G.
- On receiving a registration request from the UE the SEAF sends an authentication request (Nausf UEAuthentication authenticate Request)message to the AUSF with the serving network name (SNN) and either SUPI, if available and 5G-GUTI is valid, or SUCI. The SNN is a concatenation of service code and the Serving Network Identity (SN Id).
- Upon receiving the authentication request, the AUSF checks whether the requesting SEAF is authorized to use the SNN which is a form of home control in 5G. If the serving network is not authorized to use the SNN, the AUSF respond with “serving network not authorized” in the authentication response (Nausf UEAuthentication authenticate Response).
- The authentication information request (Nudm UEAuthentication Get Request) from AUSF to UDM/ARPF/SIDF includes the SUCI or SUPI and the SNN. SIDF is invoked to de-conceal the SUPI from SUCI. Based on SUPI and the subscription data, the UDM/ARPF choose the authentication method to be used.
- In phase 2, on selection of authentication methods, mutual authentication takes place. The authentication procedure involved in 5G.
briefly explained in the following steps for both EAP-AKA’ and 5G AKA.- Authentication Vector (AV) generation:
- EAP-AKA: The authentication procedure is followed as discussed in RFC 5448 except the authentication vector (AV) derivation at the UDM/ARPF. The UDM/ARPF first generates an AV with AMF separation bit = 1 and generates CK’ and IK’ from CK, IK and SNN. The UDM/ARPF subsequently sends this transformed AV (RAND, AUTN, XRES, CK’, IK’) to the AUSF with an indication that the AV is to be used for EAP-AKA’.
- 5G AKA: The UDM/ARPF derives the KAUSF from CK, IK and SNN and generates the 5G Home Environment AV (5G HE AV) where the 5G HE AV contains the RAND, AUTN, XRES*, and KAUSF. 5G HE AV is sent to the AUSF in the authentication information Request Response message. The AUSF stores the KAUSF and XRES* until expiry.
- The AUSF derives the KSEAF (anchor key) from KAUSF and sends the Challenge message to the SEAF in a Nausf_UE_Authentication_Authenticate Response message with KSEAF, AUTN and RAND. In case of 5G AKA HXRES* is also sent.
- On receiving of the RAND and AUTN, the USIM computes a response RES and returns RES, CK, IK to the UE. In case of 5G AKA additionally the ME compute RES* from RES. The UE then sends the Challenge Response message to the SEAF in a NAS message Authentication Response message.
- The SEAF forwards the Response Challenge message to the AUSF in Nausf UE_authentication authenticate Request message. In case of 5G AKA the SEAF computes HRES* from RES*, and compares HRES* with HXRES*. If the values are same, the SEAF considers the authentication as successful and sends the received RES*, in a Nausf_UE_authentication authenticate Request message containing the SUPI or SUCI and the SNN, to the AUSF.
- The AUSF verifies the message to support increased home control and if the verification is successful, the AUSF acts according to the authentication method as explained below. Note that if the AUSF received SUCI from the SEAF, then the AUSF also includes the SUPI in 5G-Authentication Confirmation Answer message.
- EAP-AKA: The AUSF and UDM in the home network obtains confirmation that the UE has been successfully authenticated when the EAP-Response/AKA’-Challenge received by the AUSF has been successfully verified. The AUSF derives EMSK from CK’ and IK’ as described in RFC 5448. The AUSF then uses the first 256 bits of EMSK as the KAUSF and derives the anchor key KSEAF from KAUSF. The AUSF sends EAP Success message to the SEAF inside Nausf_UEAuthentication Authenticate Response along with the KSEAF.
- 5G AKA: The AUSF compares the received RES* with the stored XRES* and if they are equal, the AUSF considers the confirmation message as successfully verified and indicates this to the SEAF.
- The AUSF and UDM in the home network obtains confirmation that the UE has been successfully authenticated.
- The SEAF sends the Success message to the UE in the N1 message.
- The SEAF then derives the KAMF from the KSEAF and the SUPI and send it to the AMF. On receiving the Success message, the UE derives KAUSF and KSEAF in the same way as the AUSF and derives the KAMF from the KSEAF and the SUPI. The SEAF provide the ngKSI and the KAMF to the AMF.
- Authentication Vector (AV) generation:
- 5G Key Hierarchy: To added
5G and 4G Authentication and Key Management Comparison
Related Posts
- 5G System Connection Management: CM-Idle and CM-Connected
- 5G NR Global Unique Temporary Identifier (GUTI)
- 5G Identifiers SUPI and SUCI
- 5G Core (5GC) Characteristics
- 5G NR RRC Procedure and Its states